
|
Vol 74 |
Page 9 |
Privacy Policy | Editorial Policy | Profit Policy | Join the Association | List of Members | Contact us | Index | Links
Back Go to page: 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 Forward

Allan George's Gems.
Contents
Apollo 11 lunar module's computer.
Does a VPN make your browsing private?
How to access the Firefox screenshot tool.
The coal fired power station furphy.
Why we wear Rosemary on ANZAC Day.
Why we wear rosemary, an ancient symbol of remembrance, on ANZAC Day.
ANZAC Day is one of the most iconic days of the Australian calendar, packed full of military traditions and ceremonial rituals, but what do a lot of them mean and what the significance of each.
Wearing rosemary.

This scent-packed herb is an ancient symbol of fidelity and remembrance, so it’s fitting that it’s become the commemorative symbol for ANZAC Day (the red poppy is worn for Remembrance Day), helping us remember those who served and the fallen. Rosemary grows wild on the Gallipoli peninsula in Turkey, where many Australians served in World War I and from where the ANZAC legend was born. In the 1980s, cuttings from shrubs in Gallipoli were planted in nurseries and sold throughout Australia to support Avenues of Honour.
Rosemary is an emblem of remembrance. It is traditional on ANZAC Day to wear a sprig of rosemary pinned to the breast or lapel (it does not matter which side, but left seems most common), or held in place by medals.
ANZAC biscuits.
The origin and invention of this sweet ANZAC treat is a hotly contested subject.

Made from oats and golden syrup, these biscuits are a far cry from the hardtack biscuit rations supplied to Diggers in Gallipoli, which were savoury and used for sustenance in the absence of perishable foods.
From the 1920s onwards, Australian recipe books nearly always included ANZAC biscuits but exactly how this recipe became identified with ANZAC, or WWI, is unknown. Since they keep pretty well before going stale, it’s believed they became an accepted addition to comfort/care packages sent to our troops overseas.
Australians love to make these biscuits to commemorate ANZAC Day and many take immense pride in their family recipes. The big question is: do you prefer your biscuits crunchy, or chewy?
Best ANZAC biscuit recipe:
-
1 cup (90g) rolled oats
-
1 cup (150g) plain flour
-
1 cup (220g) firmly packed brown sugar
-
½ cup (40g) desiccated coconut
-
125g (4 ounces) butter, chopped
-
2 Tbsp golden syrup
-
1½ Tbsp water
-
½ tsp bicarbonate of soda
Method:
-
Preheat oven to 160°C. Grease biscuit trays and line with baking paper.
-
Combine oats, sifted flour, sugar and coconut in a large bowl. Place butter, syrup (spray the measuring spoon with cooking oil, so all the syrup comes away) and the water in a small saucepan; stir over low heat until smooth. Stir in bi-carb, then stir in dry ingredients.
-
Roll level tablespoons of mixture into balls; place 5cm apart on trays, flatten slightly. Bake for 20 minutes or until golden; cool on trays.
Your biscuits should feel soft to touch, even when they’re done; they will become firmer on cooling. If you like the biscuits soft, decrease the oven temperature and/or the baking time; experiment with a few biscuits until you achieve the texture you like best. Make a note on the recipe of the time and oven temperature that the biscuits were baked.
Wearing of medals.
The awarding of medals remains one of the most time-honoured, cherished, and sacred traditions in the culture and history of the Australian Defence Force. Only the women and men who were issued medals may claim them as their own – by wearing them on their left breast. Family members of veterans, who did not earn the medals but choose to honour their loved ones by wearing them, may do so on the right breast.
If you spot someone wearing medals on each breast, it is safe to assume they are wearing their own on the left and a relative’s on the right.
The medals and the ribbons they come attached to provide a very unique roadmap of each veteran’s service history. At a glance, veterans can see which service and unit the wearer was attached to, where they served, if they deployed overseas on operations, as well as whether they served with great honour, bravery or distinction. Some medals denote extraordinary service in aerial flight, some are specific to ground operations, while others are reserved only for those who served at sea.
The Dawn Service.
The incredibly moving Dawn Service is a public ceremony, with involvement across all three services of the Australian Defence Force. It is the first commemorative event of ANZAC Day and begins before sunrise, starting at a time that allows the minute’s silence to fall at dawn. The significance of this is that it’s the same time of day that the ANZACs first landed on the beach at Gallipoli.

However, the origin stems back to the traditional military stand-to: a state of readiness assumed by ground troops at dawn and dusk in wartime, in case of a surprise enemy attack. Where and when the first Dawn Service took place is another hotly contested debate, but the 1923 Dawn Service in Albany WA, conducted by the Reverend Arthur White, Rector of St John’s Church and a former padre with the 44th Battalion on the Western Front, is a strong frontrunner for the honour.
The Ode.
The Ode comes from the fourth stanza of the poem “For The Fallen”, by the English poet and writer Laurence Binyon. It was first published in 1914 and, by 1921, had been adopted for use at Australian commemorative services.
They shall grow not old, as we that are left grow old;
Age shall not weary them, nor the years condemn.
At the going down of the sun and in the morning, we will remember them.
At ANZAC Day commemorations, an invited speaker often recites The Ode and upon completion, attendees repeat the last words “We will remember them”. After a short pause, this is followed by “Lest we forget”.
The Last Post.
A lone bugler sounding the Last Post has become one of the most distinctive sounds in the world. Eerie and evocative, it exists beyond all the usual barriers of nation, religion, race and class, charged with the memory of generations of the fallen. This is one of a number of bugle calls in the military tradition to mark phases of the day. Traditionally, it signifies the end of the day’s activities.

Bugler David Scott.
The Last Post was incorporated into funeral and memorial services as a final farewell and symbolises that the duty of the fallen is over and that they can now rest in peace.
On ANZAC Day, it is followed by one minute’s silence, then a second bugle call, The Rouse.
Laying a wreath of flowers.
A wreath or a small bunch of flowers is traditionally placed on memorials in memory of the fallen. They usually contain laurel, the traditional symbol of honour, and rosemary, or they may be native or other flowers. Wreath-laying also comes with its own protocols, with representatives for the Governor, State Government, ex-service organisations such as RSL and the ADF called up individually to lay their tributes first. All attendees are invited to lay wreaths once the dignitaries have moved through.
If laying a wreath, here’s what to do:
-
Move up to the memorial with the wreath in both hands, entering from the left;
-
Halt, pause, bend at the knees and gently lay the wreath;
-
Upon rising, adopt the attention position before taking one pace to the rear, pausing and then saluting (if wearing military uniform and headdress). For those not in uniform, it is customary after taking one pace rearwards to bow your head and pause to remember after taking the one pace rearwards. Pause again and move away from the memorial to the right.
Gunfire Breakfast.

The Gunfire Breakfast was the name given to the breakfast that the troops had prior to a morning battle – and was named as such by the Brits. During WWI, this breakfast may have consisted of biscuits and jam, or tinned bully beef, served with coffee laced with rum or condensed milk. It was prepared and eaten in darkness to the likely sound of exploding munitions and served cold as any fires or smoke would have given away their position to the enemy.
The breakfast has since evolved into a more recognisable hot meal with lashings of bacon, sausages, eggs, beans, tomatoes, damper and tea. Rum is often added to coffee or cold milk as an accompanying drink.
Today, this ANZAC Day tradition usually follows straight after the Dawn Service, with the community invited to partake in exchange for a small donation to charity.
The March.
From cities to small country towns, the March carries enormous weight with Defence veterans, as a way to honour those friends and comrades they have lost along the way.
It became popular in the 1920s for veterans who saw active service to honour their mates, but was later relaxed to include those who served in Australia in the armed services or land armies during WWII. Today it is run by RSLs and has been relaxed further, with some encouragement or acceptance of children, grandchildren and great-grandchildren marching, to assist aged veterans or to represent relatives. Veterans of Allied defence groups are now also invited to March.
Two-up
It’s customary for veterans to gather after the March to catch up with their service buddies over a beer or a meal, with reunions and lunches put on by local establishments. This is also the one day of year that the traditional game of two-up may be legally played at venues.
Bets are placed on how two pennies, thrown into the air off a section of wood called a kip, will fall. The Ringer (in charge) is usually responsible for explaining the rules and betting procedures. Only people of legal gambling age are welcome to participate, with the Ringer calling “Come in spinner” when all bets are placed and the coins are ready to be tossed.
In World War I, Australian soldiers played the game in trenches and on troop ships, so it has a strong association with ANZAC Day. The game was also played to celebrate the return of the soldiers.
How to play:
-
A designated ‘spinner’ tosses two coins into the air off a bit of wood known as a ‘kip’.
-
The players stand in a circle known as the ‘ring’. They will bet on whether the coins will fall on both heads, both tails, or a head and a tail (known as odds).
-
Two heads mean the spinner wins; two tails mean the spinner loses their bet and the right to spin; while odds mean the spinner throws again.
-
The coins must rotate 3m into the air, not touch the roof and have to fall within the ring.
-
The other members around the ring place side bets against each other on whether the spinner will win or lose, and the results of the next throw.
Lest we forget!
The villagers, seeing that there were many monkeys around, went out to the forest and started catching them. A businessman bought thousands at $10 and as supply started to diminish, the villagers stopped their effort. He further announced that he would now buy at $20. This renewed the efforts of the villagers and they started catching monkeys again. Soon the supply diminished even further and people started going back to their farms. The offer increased to $25 each and the supply of monkeys became so little that it was an effort to even see a monkey, let alone catch it!
The businessman now announced that he would buy monkeys at $50! However, since he had to go to the city for a few days, his assistant would now buy on behalf of him. In the absence of the man, the assistant told the villagers; "Look at all these monkeys in the big cage that the man has collected. I will sell them to you at $35 and when the man returns from the city, you can sell them to him for $50 each." The villagers rolled up with all their savings and bought all the monkeys. They never saw the man nor his assistant again, only monkeys everywhere!
Now you have a better understanding of how the cryptocurrency market works.
Mirages for sale.
When the RAAF had finished with their Mirages, they were stored at Woomera, given a wash and polish and put up for sale. You can see that below.
Apollo Moon Landing.
Apollo's moon-landing project was conducted by the U.S. National Aeronautics and Space Administration in the 1960s and ’70s. The Apollo program was announced in May 1961, but the choice among competing techniques for achieving a Moon landing and return was not resolved until considerable further study. In the method ultimately employed, a powerful launch vehicle (Saturn V rocket) placed a 50-ton spacecraft in a lunar trajectory. Several Saturn launch vehicles and accompanying spacecraft were built. The Apollo spacecraft were supplied with rocket power of their own, which allowed them to brake on approach to the Moon and go into a lunar orbit. They also were able to release a component of the spacecraft, the Lunar Module (LM), carrying its own rocket power, to land two astronauts on the Moon and bring them back to the lunar orbiting Apollo craft.
There’s been a lot written and spoken about the initial landing and the computer that got them there, but this bloke seems to have nailed it. He tells it in language we can all understand. It runs for about an hour but is definitely worth watching.
See the video below.

How to access the Firefox Screenshot Tool.
If you use Firefox as your browser, you already have a very good screen capture tool. If you’ve got a site open and you want to capture part or all of what’s on the screen, all you have to do is click the little scissor icon at the top of the screen (arrowed right). This will grey out the screen and open the tool. At the top right you’ll be given the option of either taking a copy of the full screen or selecting a part of it.
The two options are:
Save full page. This is the default, use this option if you want to save part of the screen, all you have to do is click outside the part you wish to save, draw you mouse to highlight fully the part you want then release your mouse. A window will pop up giving you the option to either cancel the save, copying it to the clipboard or downloading it. If you select download, you’ll find it by clicking the little blue down arrow – shown to the right of the red arrow in the pic above.
Save visible. If you click this option, the tool will copy the whole open screen and you will be given the same 3 save options.
If you find that your screenshot icon is missing from the tool bar, here's how to get it.
-
Right click in a clear spot in the tool bar
-
Click "Customise Toolbar"
-
Click on and hold EDIT CONTROLS then drag it to your toolbar.
-
Voila.
A woman showed an Aussie builder around her home and told him what colour she wanted each room to be painted. “This one will be a light blue,” she said in the first room. The builder nodded, walked to the front door and yelled, “GREEN SIDE UP!” He went back inside the house and followed her to the next room. “I want this one to be painted yellow,” she instructed. The builder nodded, went to the front door and yelled, “GREEN SIDE UP!” He went back inside the house and the owner told him that the next room was to be painted red. Again, he nodded, went to the front door and yelled, “GREEN SIDE UP!” When he came back inside the next time, the owner asked him: “I keep telling you what colour to paint the rooms and you keep going to the front door and yelling ‘Green side up!’ What does that mean?” The builder replied, “Oh, I have a couple of Kiwis laying turf in the front yard!”
Coal fired generator plants worldwide.
There is an email doing the rounds claiming to show the total number of coal fired power plants in major countries in the world to be 3723 and that there are a further 1892 more under construction. It then says: “Australia is planning to shut down its six remaining plants to SAVE the world.”
It’s garbage.
You’ll find the true figures HERE.
Does a VPN really make your online activity private?
VPNs are advertised as the best way, maybe even the only way, to stay private online, but is that really true? If we look beyond the marketing copy, we find a much more messy reality than what is portrayed on the homepages of VPN providers.
What Does a VPN Do?
When you connect to the internet, you access the website you want to visit by going through your Internet Service Provider‘s (ISP) network. Your ISP knows the domain you’re accessing and where you’re located, as does the website you’re visiting, although it has a rougher idea of your location. This data is stored in log files, which can record data such as your IP address, the time of your connection, and the length of time you were connected for.
This data is worth good money to marketers, and has become a source of income to ISPs and websites. Besides commercial purposes, log files can also be used to track people who use BitTorrent to illegally download files as well as people who use social media to brag about their crimes.

If you’re concerned about your privacy, perhaps because you just don’t want third parties making money off your data, one of the things you can do is use a virtual private network when you connect to the internet. When you connect to a VPN, the VPN sits in the middle and functions as an encrypted tunnel. Your internet service provider or local network can only see that you’re connected to the VPN, not what you’re accessing through the VPN. The websites you access will see the VPN’s IP address rather than your IP address. By going through this private server, both your ISP and any sites you visit will see its IP address rather than yours.
VPNs and Privacy
According to what many providers promise, VPNs are a silver bullet that will annihilate all your privacy worries with a single stroke. Replacing your IP address with the VPN’s, however, solves only one problem, and not even a big one at that. There are still plenty of ways to find out who you are and what you’re doing.
Probably the biggest problem VPNs don’t solve is that you can still be “seen” thanks to browser cookies which websites use to remember who you are, as well as any social media accounts you’re signed in to, and many keep you signed in, like it or not. This means that if you’re signed in to Google or Facebook when you’re using your browser with a VPN, they can still track you. It’ll just look like your physical location has changed.
The only way to fix this is by using Incognito Mode and a VPN together, but we have yet to find the VPN provider that will tell you this.
In fact, finding out anything about how VPNs operate is hard: For whatever reason, they don’t like to share details about how their products or businesses work. One thing that’s very hard to test, for example, is how secure the connection a VPN provides actually is.
For example, one of the biggest promises they make is that your connection will be encrypted in something called a “secure tunnel.” That sounds really cool, until you realize that there’s no good way to test whether it works from the outside. Though the AES-256 cipher most tunnels are advertised as being encrypted with is nigh uncrackable, there’s no good way to find out whether it really is that encryption key that’s being used.
VPNs and Logs
This brings us to another thing that we’re asked to take on faith. Namely, how your logs are treated. Many VPNs claim to be “no-logs” or “zero-logs” services, saying that they do not keep records of your activity online, however, this claim takes some stretching of the imagination to believe, as there’s always a record of the event when servers connect. The internet literally cannot function without this data being generated. It has to be kept (at least temporarily) so that servers know where to send data back and forth.
We suspect that most of these services destroy logs as soon as they’re created, which is fine from a privacy perspective, but doesn’t fit well into marketing copy. Many VPNs will admit to logging some types of data, though that usually comes with assurances that they only log unimportant information, like what time the VPN server connected. The log files that could identify users are supposedly not recorded or destroyed, like with a zero-logs service.
Whether you’re going with a no-logs service or one that keeps only connection logs, you’re taking the VPN provider on faith, as neither claim can be investigated. In the end, you’re going to have to trust that VPNs aren’t selling your data. Look for a VPN with a good reputation, not one that just promises “no logs”. Some VPNs work with third-party auditors in an attempt to prove their security promises.
What is a No-Log VPN, and why is that important for Privacy?
What Are VPNs Good for?
With all of the above information in mind, the question arises whether VPNs are actually good for anything. They are, in fact, very useful tools, they’re just not the privacy panacea that they’re often said to be. Generally speaking, there are four reasons to use a VPN:
-
As a privacy tool in a wider strategy: If all you do is turn on a VPN and keep browsing like normal, a VPN won’t necessarily give you much privacy. But combined with Incognito Mode, secure email and messaging, plus some other tricks, you’ll be much harder to track.
-
As a way to circumvent regional restrictions: You can unlock any country’s Netflix library, for instance, or visit the sites of state broadcasters in other countries.
-
To stay ahead of copyright enforcers: People who illegally download copyrighted content using software like BitTorrent often use VPNs to disguise their peer-to-peer traffic.
-
To circumvent censorship: People that live in countries with internet restrictions, China, for example, can use a VPN to get away from their country’s internet and onto the “real,” unfiltered one.
VPNs are handy tools, but they’re not the only way to protect yourself online—nor even the best one. Although VPNs definitely have a use for most people who spend a lot of time on the internet, their use (like with any tool) is a lot more precise than many would have you believe.
If you’re looking for a VPN to protect your privacy, you could try ExpressVPN. ExpressVPN is a stable company that has been around for years, and many people have used it for that long. It’s not a freeby, you have to pay for it, but if privacy is your thing then ExoressVPN could be the answer.
How do VPN’s work?
A VPN, or Virtual Private Network, allows you to create a secure connection to another network over the Internet. VPNs can be used to access region-restricted websites, shield your browsing activity from prying eyes on public Wi-Fi, and more. These days VPNs are really popular, but not for the reasons they were originally created. They originally were just a way to connect business networks together securely over the internet or allow you to access a business network from home.

VPNs essentially forward all your network traffic to the network, which is where the benefits, like accessing local network resources remotely and bypassing Internet censorship, all come from. Most operating systems have integrated VPN support.
What Is a VPN and how does it help me?
In very simple terms, a VPN connects your PC, smartphone, or tablet to another computer (called a server) somewhere on the internet and allows you to browse the internet using that computer’s internet connection. So, if that server is in a different country, it will appear as if you are coming from that country and you can potentially access things that you couldn’t normally.
So how does this help you?
You can use a VPN to:
-
Bypass geographic restrictions on websites or streaming audio and video.
-
Watch streaming media like Netflix and Hulu.
-
Protect yourself from snooping on untrustworthy Wi-Fi hotspots.
-
Gain at least some anonymity online by hiding your true location.
-
Protect yourself from being logged while torrenting.
Many people these days are using a VPN for torrenting or bypassing geographic restrictions to watch content in a different country. They are still very useful for protecting yourself while working at a coffee shop, but that’s hardly the only use anymore.
How do you get a VPN, and which one should you choose?
Depending on your needs, you can either use a VPN from your workplace, create a VPN server yourself, or sometimes host one out of your house, but realistically the vast majority of people are just looking for something to protect them while torrenting or help them watch some media online that they can’t seem to access from their country. The easiest thing to do is simply head to one of these sites, sign up, and download the VPN client for your Windows PC, Mac, Android, iPhone, or iPad. It’s as easy as that. You could use ExpressVPN which we mentioned earlier.
How Does a VPN work?
When you connect your computer (or another device, such as a smartphone or tablet) to a VPN, the computer acts as if it’s on the same local network as the VPN. All your network traffic is sent over a secure connection to the VPN. Because your computer behaves as if it’s on the network, this allows you to securely access local network resources even when you’re on the other side of the world. You’ll also be able to use the Internet as if you were present at the VPN’s location, which has some benefits if you’re using public Wi-Fi or want to access geo-blocked websites.
When you browse the web while connected to a VPN, your computer contacts the website through the encrypted VPN connection. The VPN forwards the request for you and forwards the response from the website back through the secure connection. If you’re using a USA-based VPN to access Netflix, Netflix will see your connection as coming from within the USA.
Other example uses for VPNs
VPNs are a fairly simple tool, but they can be used to do a wide variety of things:
-
Access a Business Network while travelling: VPNs are frequently used by business travellers to access their business’ network, including all its local network resources, while on the road. The local resources don’t have to be exposed directly to the Internet, which increases security.
-
Access your home network while traveling: You can also set up your own VPN to access your own network while traveling. This will allow you to access a Windows Remote Desktop over the Internet, use local file shares, and play games over the Internet as if you were on the same LAN (local area network).
-
Hide your browsing activity from your local network and ISP: If you’re using a public Wi-Fi connection, your browsing activity on non-HTTPS websites is visible to everyone nearby, if they know how to look. If you want to hide your browsing activity for a bit more privacy, you can connect to a VPN. The local network will only see a single, secure VPN connection. All the other traffic will travel over the VPN connection. While this can be used to bypass connection-monitoring by your Internet service provider, bear in mind that VPN providers may opt to log the traffic on their ends.

-
Access Geo-Blocked Websites: Whether you’re trying to access your Netflix account while traveling out of the country or you wish you could use American media sites like Netflix, Pandora, and Hulu, you’ll be able to access these region-restricted services if you connect to a VPN located in that country.
-
Bypass Internet Censorship: Many Chinese people use VPNs to get around the Great Firewall of China and gain access to the entire Internet. (However, the Great Firewall has apparently started interfering with VPNs recently.)
-
Downloading Files: Yes, let’s be honest, many people use VPN connections to download files via BitTorrent. This can actually be useful even if you’re downloading completely legal torrents, if your ISP is throttling BitTorrent and making it extremely slow, you can use BitTorrent on a VPN to get faster speeds. The same is true for other types of traffic your ISP might interfere with (unless they interfere with VPN traffic itself.)
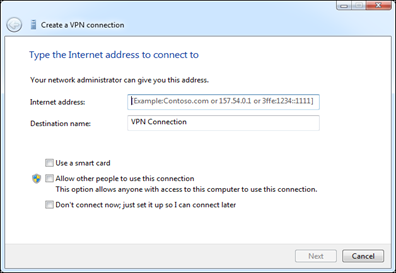
How to set up a VPN in Windows
Connecting to a VPN is fairly simple. In Windows, press the Windows key, type VPN in the window at the bottom left of your screen and click the "Add a VPN Connection" option that will appear at the top of your screen.
(If you use Windows 8, you’ll have to click the Settings category after searching.)
Click the big + that appears at the top of your screen then enter the address and login credentials of the VPN service you want to use. You can then connect to and disconnect from VPNs using the network icon in the system tray, the same one where you manage the Wi-Fi networks you’re connected to.
A man met a beautiful blonde lady and after a short courtship asked her to marry him. She said, ‘But we don’t know anything about each other.’ He said, ‘That’s all right, we’ll learn about each other as we go along.’ So she consented, they were married, and off they went on a honeymoon at a resort. One morning they were lying by the pool, when he got up off of his towel, climbed up to the 10 metre board and did a two and a half tuck, followed by three rotations in the pike position, at which point he straightened out and cut the water like a knife. After a few more demonstrations, he came back and lay down on the towel. She said, ‘That was incredible!’ He said, ‘I used to be an Olympic diving champion. You see, I told you we’d learn more about each other as we went along.’ So she got up, jumped in the pool and started doing laps. After seventy- five laps she climbed out of the pool, lay down on her towel and was hardly out of breath. He said, ‘That was incredible! Were you an Olympic endurance swimmer?’ ‘No,’ she said, ‘I was a prostitute in Mildura, but I worked both sides of the Murray River

Velly Intelesting - but stoopid!!
Back Go to page: 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 Forward